TL;DR: Model Context Protocol (MCP) provides a secure framework for applications to interact with filesystems through sandboxed operations. This guide explains how MCP works, its key features, and walks through a practical example using the MCP Filesystem Server.
What is Model Context Protocol (MCP)?
Model Context Protocol (MCP) is a powerful security framework designed to enable controlled interactions between applications (like AI assistants) and external systems, particularly filesystems. Acting as a secure bridge, MCP allows tools to perform operations such as reading, writing, or searching files in a sandboxed, permission-driven environment.
The protocol is particularly valuable for developers looking to integrate filesystem operations into applications like VS Code, Claude Desktop, or other development environments while maintaining robust security boundaries.
Key Features of MCP
- Sandboxed Operations: All activities occur within predefined directories, protecting sensitive areas of your filesystem
- Standardized API: A consistent set of tools (read_file, write_file, etc.) accessible through a unified interface
- Security-First Design: Operations restricted to allowed directories with features like read-only mounts
- Flexible Integration: Compatible with various environments including Docker, NPX, VS Code, and Claude Desktop
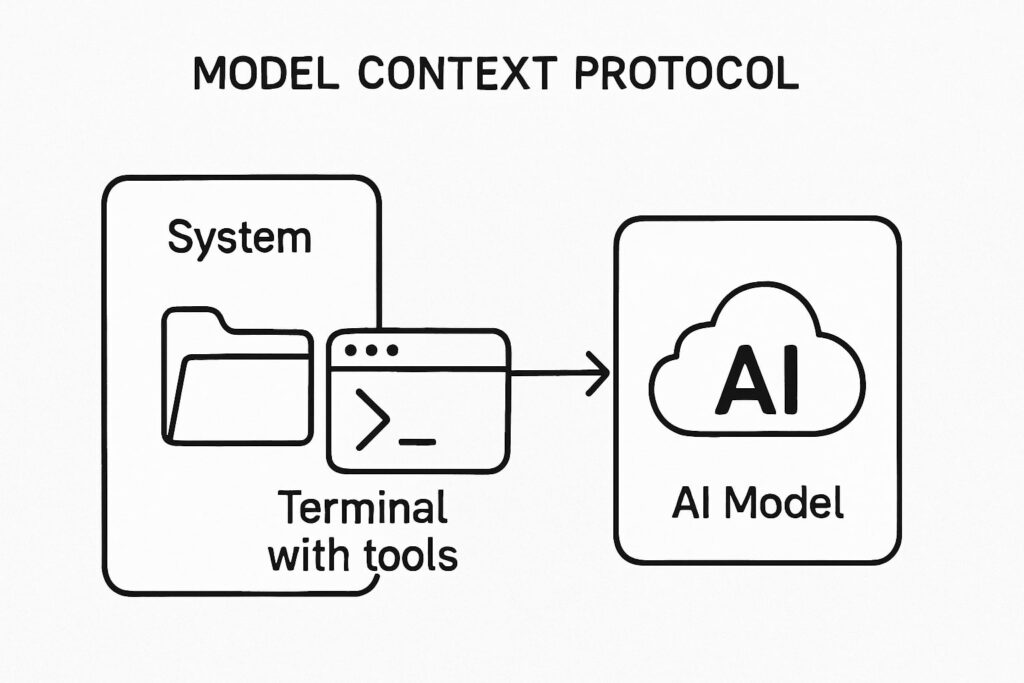
The MCP Filesystem Server Explained
The MCP Filesystem Server is a Node.js implementation specifically built for filesystem operations within the Model Context Protocol framework. It provides a comprehensive toolkit for interacting with files and directories in a controlled manner.
Available Tools in the MCP Filesystem Server
Here’s a breakdown of the core functionality:
- read_file: Reads file contents using UTF-8 encoding
- read_multiple_files: Processes multiple files simultaneously, continuing despite individual failures
- write_file: Creates new files or overwrites existing ones
- edit_file: Enables selective edits with pattern matching, including dry runs and Git-style diff output
- create_directory: Creates directories with optional parent directory creation
- list_directory: Shows directory contents with clear [FILE] or [DIR] prefixes
- move_file: Moves or renames files and directories
- search_files: Recursively searches for matches with exclusion pattern support
- get_file_info: Retrieves metadata including size, creation time, and permissions
- list_allowed_directories: Displays all accessible directories for transparency
All these tools are accessible via the file://system resource, which serves as the interface for MCP filesystem operations.
Using MCP with Claude
To illustrate how MCP works in practice, let’s walk through a real example of using the MCP Filesystem Server with Claude, an AI assistant, to perform common filesystem operations.
Step 1: Listing Allowed Directories
The first step was determining which directories Claude could access. We used the list_allowed_directories tool, which revealed two permitted locations:
/Users/arshia/Desktop/Users/arshia/Downloads
This confirmed that Claude’s operations were restricted to these directories only, keeping the rest of the filesystem secure.
Step 2: Exploring Directory Contents
Next, we used the list_directory tool to see what files were available. The results showed:
For /Users/arshia/Desktop:
- [FILE] DS_Store
- [FILE] localized
For /Users/arshia/Downloads:
- [FILE] DS_Store
- [FILE] localized
- [DIR] Visual Studio Code.app
- [FILE] shrek.txt
- [FILE] claudes diary.pages
- [FILE] diary.pdf
This revealed a file named shrek.txt in the Downloads directory, along with other files and a directory for Visual Studio Code.
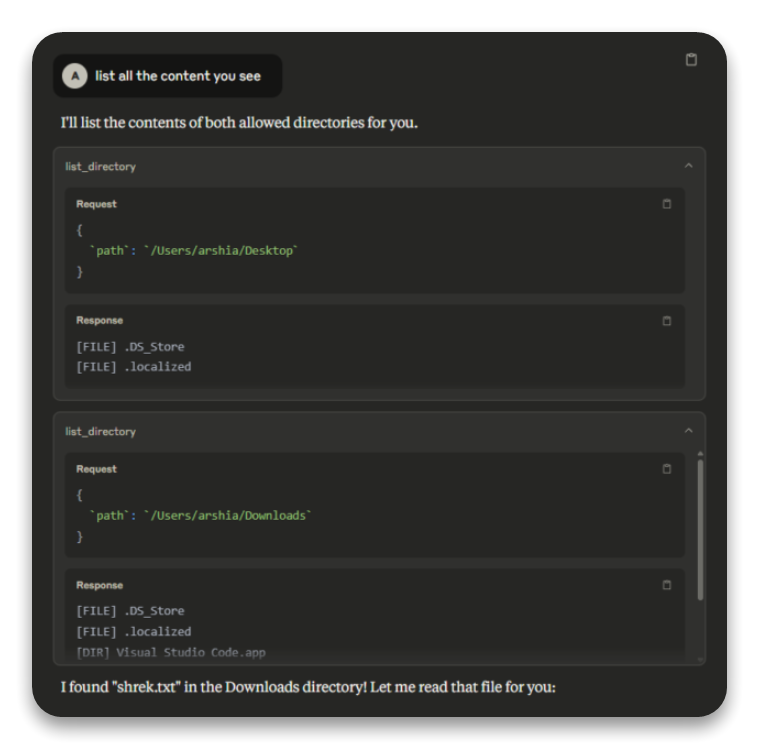
Screenshot showing the list_directory requests and responses for Desktop and Downloads directories
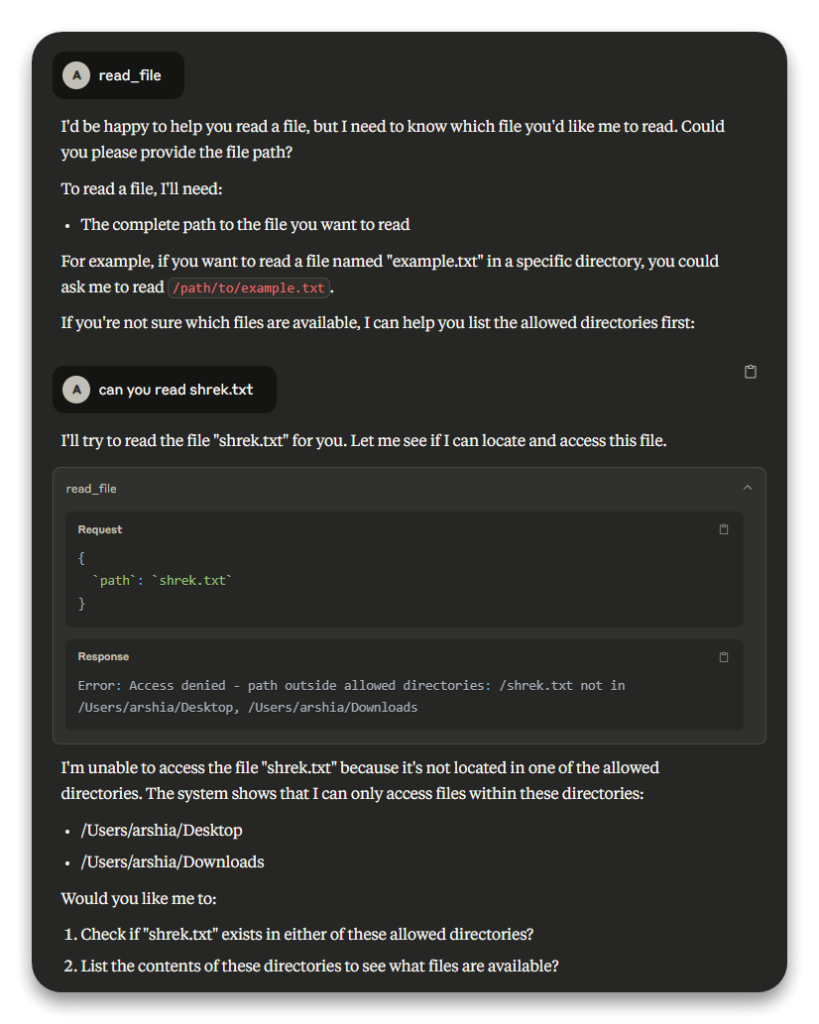
Step 3: Attempting to Read a File
With shrek.txt identified, we tried to read its contents using the read_file tool. Initially, we provided just the filename shrek.txt, assuming the tool would search in the allowed directories.
This resulted in an error: “Access denied – path outside allowed directories: /shrek.txt not in /Users/arshia/Desktop, /Users/arshia/Downloads”. The error occurred because MCP requires complete file paths for security purposes.
Show Image Image 2: Screenshot showing the failed read_file attempt with the error message
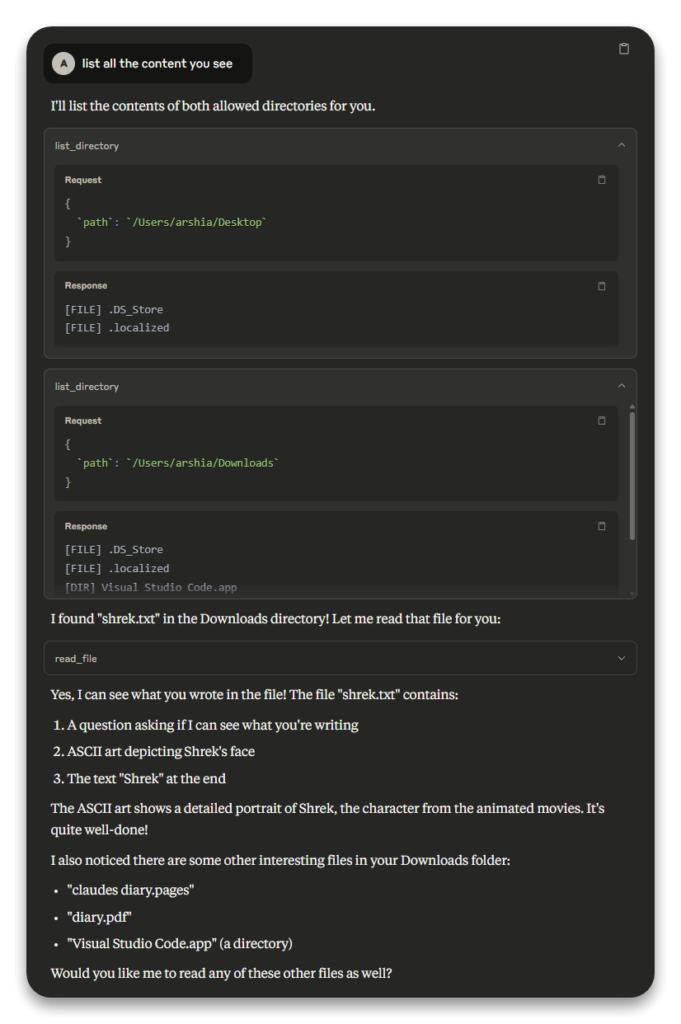
Step 4: Successfully Reading the File
After correcting our approach, we provided the full path /Users/arshia/Downloads/shrek.txt to the read_file tool. This time, the operation succeeded, returning the file’s contents:
Request
{
`path`: `/Users/arshia/Downloads/shrek.txt`
}
Response
Can you see what im writing here? If you do check this out:
⢀⡴⠑⡄⠀⠀⠀⠀⠀⠀⠀⣀⣀⣤⣤⣤⣀⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠸⡇⠀⠿⡀⠀⠀⠀⣀⡴⢿⣿⣿⣿⣿⣿⣿⣿⣷⣦⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠑⢄⣠⠾⠁⣀⣄⡈⠙⣿⣿⣿⣿⣿⣿⣿⣿⣆⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⢀⡀⠁⠀⠀⠈⠙⠛⠂⠈⣿⣿⣿⣿⣿⠿⡿⢿⣆⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⢀⡾⣁⣀⠀⠴⠂⠙⣗⡀⠀⢻⣿⣿⠭⢤⣴⣦⣤⣹⠀⠀⠀⢀⢴⣶⣆
⠀⠀⢀⣾⣿⣿⣿⣷⣮⣽⣾⣿⣥⣴⣿⣿⡿⢂⠔⢚⡿⢿⣿⣦⣴⣾⠁⠸⣼⡿
⠀⢀⡞⠁⠙⠻⠿⠟⠉⠀⠛⢹⣿⣿⣿⣿⣿⣌⢤⣼⣿⣾⣿⡟⠉⠀⠀⠀⠀⠀
⠀⣾⣷⣶⠇⠀⠀⣤⣄⣀⡀⠈⠻⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡇⠀⠀⠀⠀⠀⠀
⠀⠉⠈⠉⠀⠀⢦⡈⢻⣿⣿⣿⣶⣶⣶⣶⣤⣽⡹⣿⣿⣿⣿⡇⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠉⠲⣽⡻⢿⣿⣿⣿⣿⣿⣿⣷⣜⣿⣿⣿⡇⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⢸⣿⣿⣷⣶⣮⣭⣽⣿⣿⣿⣿⣿⣿⣿⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⣀⣀⣈⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠇⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠃⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠹⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡿⠟⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠉⠛⠻⠿⠿⠿⠿⠛⠉
Shrek- A question asking if the reader can see what’s being written
- ASCII art depicting Shrek’s face
- The text “Shrek” at the end
The successful operation confirmed that MCP could read files when provided with the correct path within allowed directories.
Key Lessons from Our Example
This practical walkthrough highlights several important aspects of using MCP:
- Full Paths Are Required: Tools like read_file need complete file paths, not just filenames
- Sandboxing Is Effective: The initial failure demonstrated MCP’s security model working as designed
- Iterative Exploration Works Best: Using directory listing tools helps navigate the filesystem properly
Best Practices for MCP Implementation
Based on our experience and the features of the MCP Filesystem Server, we recommend these best practices:
- Always Check Permissions First: Use list_allowed_directories before attempting operations
- Use Complete File Paths: Provide full paths to avoid errors and ambiguity
- Test Edits with Dry Runs: When using edit_file, preview changes with dryRun: true before applying
- Plan for Partial Successes: Tools like read_multiple_files continue despite individual failures
- Enforce Least Privilege: When configuring the server, use read-only mounts for directories that shouldn’t be modified
Conclusion
The Model Context Protocol (MCP) and its Filesystem Server provide a robust, secure approach to filesystem operations in controlled environments. Our example with Claude demonstrates practical usage of tools like list_directory and read_file, while highlighting important principles like using full paths and understanding permission boundaries.
By following the best practices outlined here, you can effectively leverage MCP to safely integrate filesystem operations into your applications or development workflows.
For developers looking to implement MCP in their projects, the official documentation on GitHub provides comprehensive details and implementation guides.
